































Image: Getty/iStockphoto
Crypto-mining malware is being hidden in fake versions of popular software distributed via free download sites and is avoiding detection by waiting for a month before it runs in a campaign that has infected Windows PCs around the world.
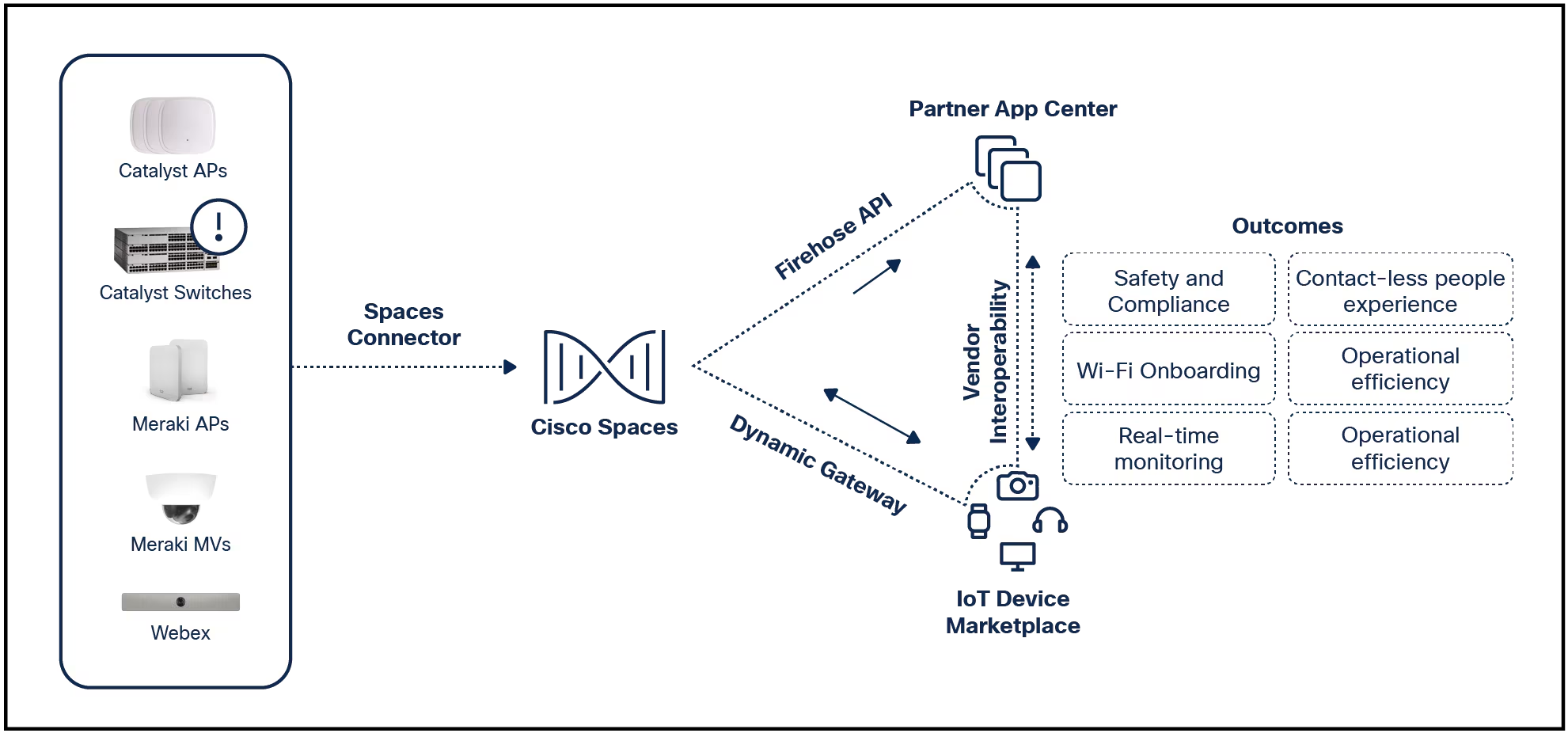
Dubbed Nitrokod, the malware campaign has been active since at least 2019 and has been detailed by cybersecurity researchers at Check Point.
Crypto miners -also known as cryptojackers -are a form of malware that secretly exploit the computing power of infected devices to mine for cryptocurrency.
The process often goes undetected and the victim of the attack doesn't receive the cryptocurrency, which is sent to the malware operator, who is likely using a large network of infected devices to generate as much cryptocurrency as possible, without the cost of using their own computing power or electricity.
SEE: A winning strategy for cybersecurity ( special report)
Nitrokod is distributed via free software download sites that researchers say can be found easily using search engines. The software downloads claim to be desktop versions of popular web applications even though they don't actually have desktop versions.
"The malware is dropped from applications that are popular, but don't have an actual desktop version such as Google Translate, keeping the malware versions in demand and exclusive," Check Point said.
But anyone who downloads these trojan applications will unwittingly find themselves infected with crypto-mining malware -but not for a month after the first download, due to a multi-stage process that delays the infection process to help ensure the attack isn't discovered.
The infection process begins when the application is downloaded via a web installer, which in turn downloads and runs a .exe installer that is used to maintain persistence on the infected machine, as well as sending information about it back to the attacker.
Five days after this, the next stage of the process delivers a dropper that monitors when the machine is restarted and, after the fourth instance, extracts another installer from an encrypted RAR file. Taking this multi-stage approach helps the malware avoid being detected in a sandbox set up by security researchers.
SEE: These are the biggest cybersecurity threats. Make sure you aren't ignoring them
At this point, evidence of the previous stages are removed from log files to avoid the installation being tracked and a scheduled task is set up to trigger after 15 days.
At that point, another encrypted RAR file is downloaded that delivers another dropper, which in turn delivers another dropper from an encrypted file and executes it -installing the crypto miner on the infected PC, a month after the initial software download.
According to Check Point, the campaign stayed hidden under the radar for years and victims around the world have inadvertently infected their machines with malware.
"What's most interesting to me is the fact that the malicious software is so popular, yet went under the radar for so long," said Maya Horowitz, VP of research at Check Point Software.
Anyone who has downloaded the applications is urged to uninstall them and remove the malicious files. To avoid falling victim to this and other trojanised software downloads, it's recommended that users only download legitimate software from trusted websites.
While cryptojackers are arguably among the least damaging forms of malware, falling victim should still be considered a risk -particularly as the same methods used to install it could be exploited to install other, more damaging forms of malware, including ransomware and password-stealing trojans.
"Currently, the threat we identified was unknowingly installing a cryptocurrency miner, which steals computer resources and leverages them for the attacker to monetize on," said Horowitz.
"Using the same attack flow, the attacker can easily choose to alter the final payload of the attack, changing it from a crypto miner to, say, ransomware or banking Trojan," she added.
 Tags chauds:
technologie
La sécurité
Tags chauds:
technologie
La sécurité