

















2,000+ That is the approximate number of cloud services that Ken Hankoff, Manager of Cisco IT Risk Management's Cloud and Application Service Provider Remediation (CASPR) Program believes Cisco's 70,000 employees use. For the last...

In our previous big data blogs, a number of my Cisco associates have talked about the right infrastructure, the right sizing, the right integrated infrastructure management and the right provisioning and orchestration for your clu...

Cisco will Leverage OPNFV Efforts in Evolved Services Platform (ESP) Development Most people following industry trends are aware of the ETSI Network Functions Virtualization (NFV) Industry Specification Group, which was formed in ...

Today's blog post is by a guest author,Adel du Toit, who is currently spearheading the effort by Cisco's internal IT organization to deliver IT-as-a-Service internally, dubbed the Cisco IT "eStore." Recently, the eStore team took ...

The Greek philosopher Epictetus once said, "We have two ears and one mouth so that we can listen twice as much as we speak." This is an important adage to embrace, especially with social media marketing programs. Listening enables...

As the number of users of social media continues to grow, the boundary between our personal and professional lives begins to overlap. Unsurprisingly, the customer buying cycle is also beginning to change. By the ti...

With all the frenzied fanfare normally surrounding the debut of new Apple products, the iPhone 6 and iPhone 6 Plus were recently introduced to the masses. And though these new phones were the big news of the day for the technology...

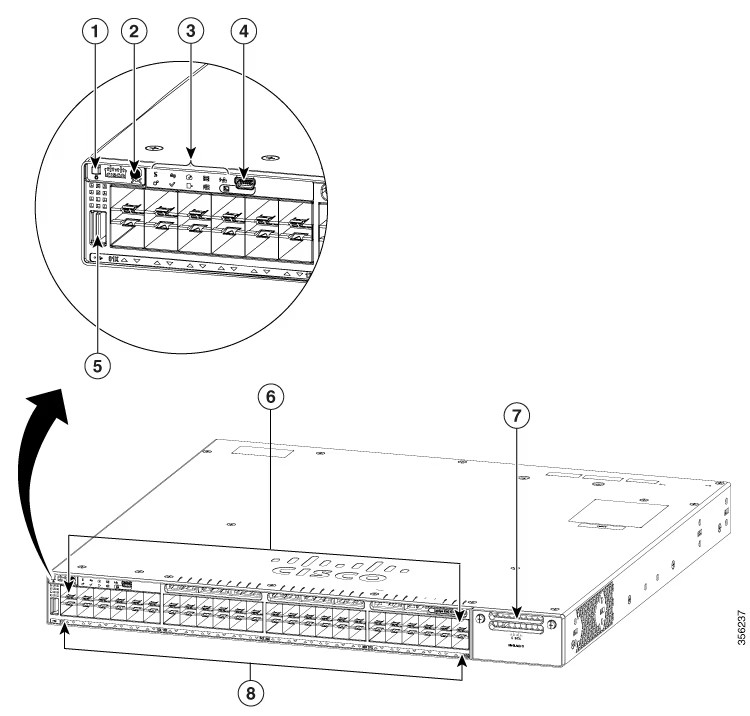
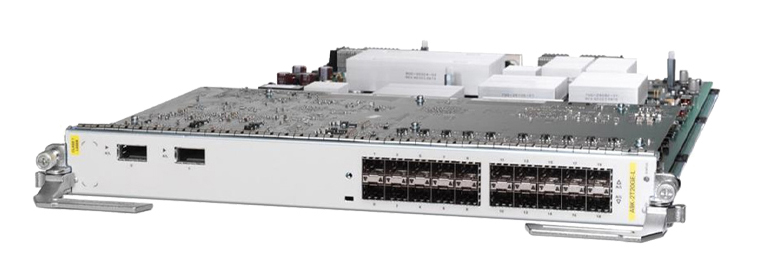
This week at Interop New York, Cisco launched to its customers and partners advancements in access routing to help partners transform businesses' networks to support cloud and mobile solutions -the new Cisco ISR 4000 Series. This ...

I recently had the pleasure to read an excellent article by one of our industry's leading analysts, Mr. Gabriel Brown of Heavy Reading titled "Analyzing Apple & VoLTE". In this article, he makes the observation, that Apple -wh...

Researchers from the Cisco Talos Security Intelligence and Research Team recently discovered an elaborate attack dubbed the String of Paerls. The attack, a combined spearphishing and exploit attempt, was able to bypass most antivi...

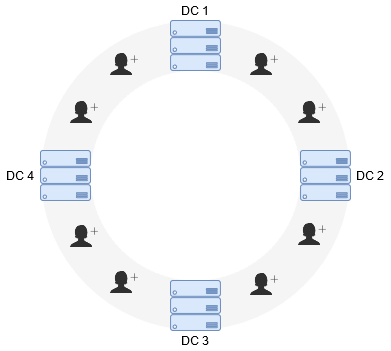
As I sit here on an airplane en-route to San Jose with my MacBook Pro at hand, heading to an industry-leading networking event (albeit on my own time, yes -this is officially vacation), I've found myself reflecting on collaboratio...

As you probably know, networking can bring your career to a new level. Who you meet can open a variety of doors -you're able to meet new clients, gain referrals, meet future peers, find a mentor, or begin a new partnership. The po...