
























 Image: AerialPerspective Images/Getty Images
Image: AerialPerspective Images/Getty Images The US Department of Commerce's technical standards organization NIST has nominated the Ascon group of cryptographic algorithms for protecting small devices and information transmitted to and from IoT devices.
NIST will later this year publish the "lightweight cryptography" standard after picking the Ascon family for the task.
Also: What is the IoT? Everything you need to know about the Internet of Things right now
It selected the algorithms to protect a vast array of devices, sensors, and actuators. The algorithms are also designed for implanted medical devices, stress detectors inside roads and bridges, and keyless entry fobs for vehicles.
Many of these devices operate with low power that the "lightweight cryptography" needs to account for when protecting information on and transmitting from them.
"The world is moving toward using small devices for lots of tasks ranging from sensing to identification to machine control, and because these small devices have limited resources, they need security that has a compact implementation," said NIST computer scientist Kerry McKay in an announcement.
"These algorithms should cover most devices that have these sorts of resource constraints."
NIST selected Ascon in 2019 as the primary candidate for lightweight authenticated encryption, so it's had lots of time to put it through tests. Ascon was developed in 2014 by a team of cryptographers from Graz University of Technology, Infineon Technologies, Lamar Security Research, and Radbound University.
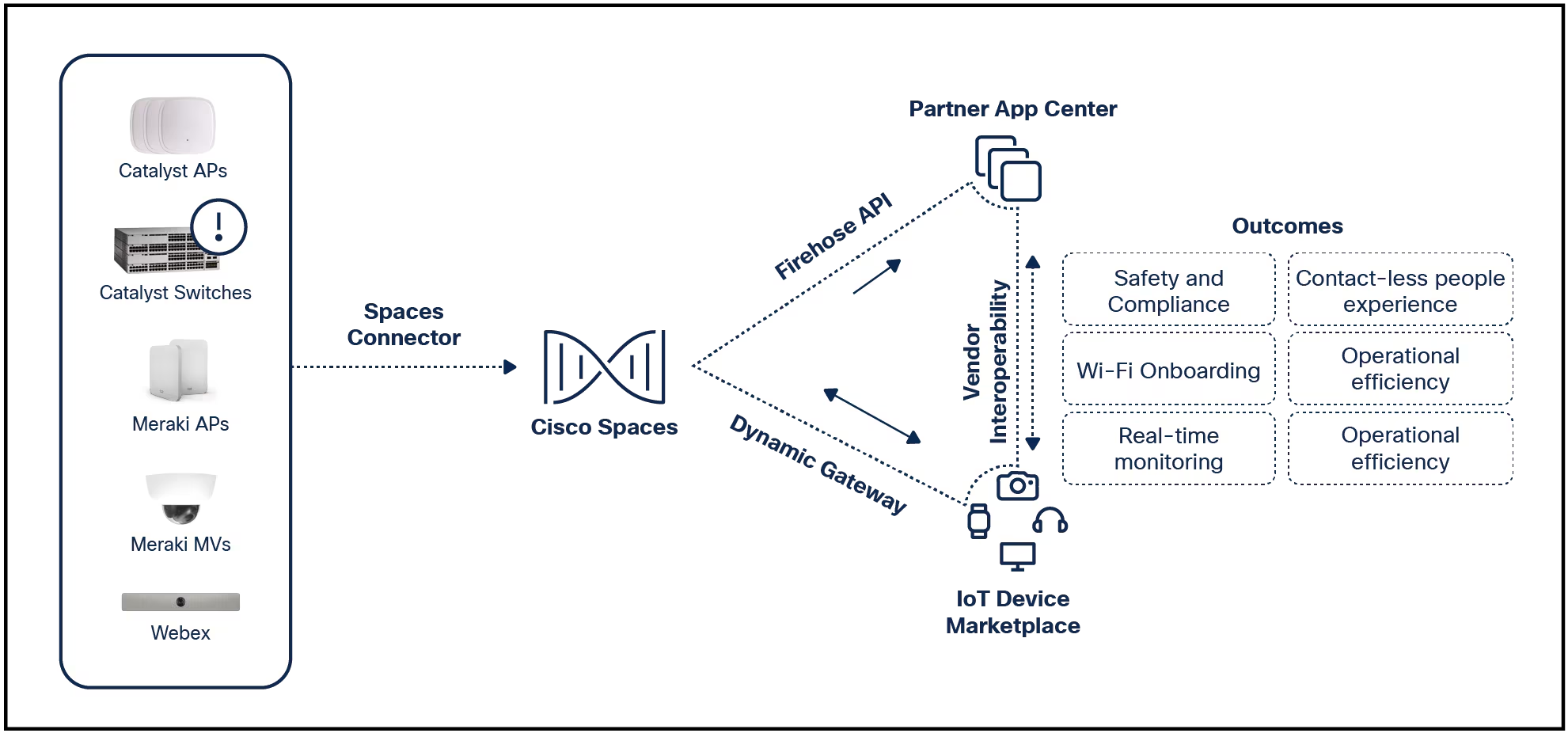
McKay noted there are seven variants in the Ascon family. Two very important ones are authenticated encryption with associated data (AEAD) and hashing.
AEAD allows a message to be encrypted while leaving the header of a message and a device's IP address in plaintext. NIST points out that AEAD can be used in vehicle-to-vehicle communications. It can also prevent spoofing messages exchanged with radio frequency identification (RFID) tags. Meanwhile, hashing could be used to check if a software update is valid and has been downloaded correctly.
Also:Testing RFID blocking cards: Do they work? Do you need one?
NIST last July announced four candidates for post-quantum resistant encryption algorithms. However, within a month, one of the algorithms was undermined by researchers who were awarded$50,000 via Microsoft's bug bounty. The algorithms are meant to protect data encrypted today that in future could be cracked by a powerful enough quantum computer.
Also: What is quantum computing? Everything you need to know about the strange world of quantum computers
McKay notes that post-quantum encryption is most important for "long-term secrets that need to be protected for years" whereas lightweight cryptography is more important for "ephemeral secrets".
 Tags chauds:
technologie
La sécurité
Tags chauds:
technologie
La sécurité