































What Is EVPN?
EVPN is a next-generation full-service bearer VPN solution. It unifies the control planes for various VPN services and uses BGP extensions to transmit Layer 2 or Layer 3 reachability information, separating the forwarding plane from the control plane.
Traditional L2VPN lacks load balancing capabilities and consumes many network resources. EVPN overcomes these drawbacks and introduces IP VPN's advantages of traffic balancing and flexible deployment into the Ethernet. EVPN is widely used for interconnecting Layer 2 networks spanning large data centers. Furthermore, it can carry L3VPN services, thereby reducing protocol complexity.
What Are EVPN and BGP EVPN?
EVPN is a next-generation full-service bearer VPN solution. It subverts the traditional L2VPN's mechanism of learning MAC addresses on the forwarding plane, introduces the control plane, and uses BGP extensions to transmit MAC address information. Based on MP-BGP, EVPN defines a series of new BGP EVPN route types that enable different sites to learn MAC addresses from each other.
BGP EVPN routes are classified into the following types:
1. Ethernet auto-discovery route
An Ethernet auto-discovery route advertises the reachability of the local PE to the MAC addresses of its connected sites. This route is mainly used in fast convergence, redundancy protection, aliasing, and split horizon scenarios to implement load balancing on a multi-homing network.
2. MAC/IP advertisement route
An EVPN MAC/IP route advertises the MAC address, IP address, and other information of sites. This eliminates the need to flood ARP requests on the network, thereby reducing the broadcast traffic volume on the network and saving bandwidth resources.
3. Inclusive multicast route
An inclusive multicast route advertises the address reachability of broadcast, unknown unicast, and multicast (BUM) traffic to implement mutual neighbor discovery in a broadcast domain. This enables the local PE to send BUM traffic received from CEs to the remote PE. Such a route also contains tunnel attributes that enable PEs to establish a tunnel between them for transmitting data plane traffic.
4. Ethernet segment route
An Ethernet segment route allows PEs connected to the same CE to discover each other. This route is mainly used for designated forwarder (DF) election. To prevent a CE multi-homed to multiple PEs from receiving duplicate traffic, only one PE is required to forward BUM traffic to the CE. Such a PE is elected among all PEs on the same Ethernet segment (ES) through DF election.
5. IP prefix route
An IP prefix route allows an EVPN to access the external network. EVPN advertises imported external routes as IP prefix routes.
Why Do We Need EVPN?
Challenges Facing Traditional L2VPN Technologies
The following uses the virtual private LAN service (VPLS) technology as an example to describe the challenges that face traditional L2VPN technologies. VPLS is an early MPLS VPN technology and has been used extensively in data center interconnection scenarios to provide multipoint-to-multipoint wide area Ethernet services for enterprise users. However, VPLS has several limitations that prevent it from meeting the requirements of large-scale and complex data centers.
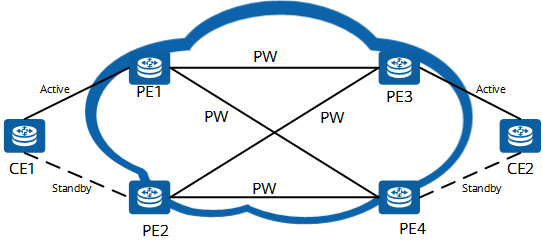
Traditional L2VPN deployment on a DCI network
Difficult network deployment
PEs need to learn the MAC addresses of all CEs but have only limited capacity in their MAC address tables. In addition, PEs need to have high specifications due to the large number of manual configurations that exist on a network.
Limited network scale
VPLS requires full-mesh PWs to be established between PEs, and is therefore unsuitable for large-scale networks.
Moreover, VPLS lacks a control plane. This means that if a MAC address change or fault occurs, the Layer 2 forwarding entries need to be re-learned through flooding, resulting in poor convergence.
Low link bandwidth utilization
PEs must work in single-active mode to ensure that loops do not form between them and CEs. Consequently, the link bandwidth utilization is low.
Benefits Brought by EVPN
EVPN solves the preceding problems as follows:
As shown in the following figure, EVPN uses BGP extensions to move MAC address learning and advertisement between Layer 2 networks from the data plane to the control plane. This allows a device to manage MAC addresses in the same way as it manages routes, making it possible to implement load balancing between EVPN routes with the same destination MAC address but different next hops.
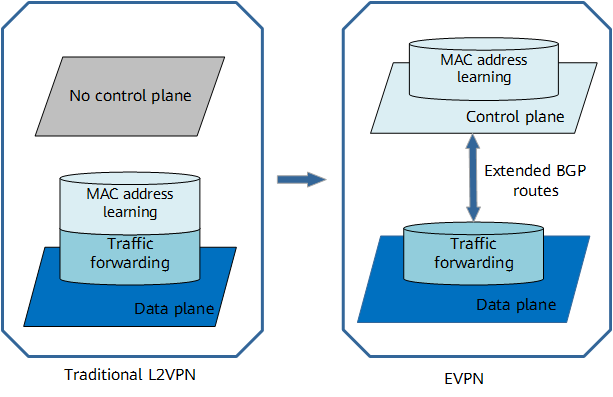
Comparison between EVPN and traditional L2VPN
EVPN eliminates the need to establish full-mesh connections between PEs. This is because PEs communicate with each other on an EVPN through BGP, which provides the route reflection function. As such, a route reflector (RR) can be deployed on an EVPN to reflect EVPN routes to PEs with which the RR has established peer relationships. This greatly reduces network complexity and the number of network signaling messages.
EVPN enables PEs to learn local MAC addresses using ARP and learn remote MAC and IP addresses using MAC/IP advertisement routes. The PEs can then store these addresses locally. After receiving an ARP request, a PE searches its locally cached MAC address and IP address information based on the destination IP address in the ARP request. After finding the corresponding information, the PE returns an ARP reply. This reduces consumption of network resources because the PE no longer needs to broadcast ARP requests to other PEs.
How Does EVPN Work?
Basic Concepts
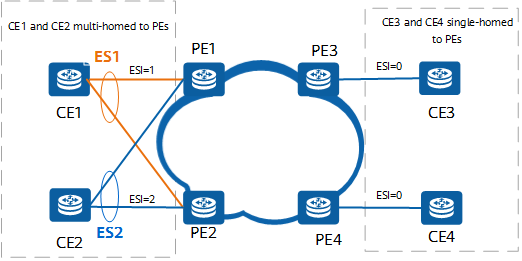
EVPN networking
ES
If a CE is multi-homed to two or more PEs, the Ethernet links that connect the CE to different PEs form an ES. On the network shown in the preceding figure, CE1 is dual-homed to PE1 and PE2, and the two Ethernet links between CE1 and PE1 and between CE1 and PE2 form an ES.
ESI
An Ethernet segment identifier (ESI) uniquely identifies an ES. On the network shown in the following figure, different PEs' interfaces connected to the same CE must have the same ESI. If the ESI is 0, the CE is singled-homed to the PE.
EVI
An EVPN instance (EVI), similar to the virtual switch instance (VSI) of VPLS, is used to identify a VPN customer. Because EVPN is a type of VPN, a PE can have multiple EVIs.
MAC-VRF
A MAC-VRF stores MAC addresses learned by an EVI through BGP extensions. Each EVI has an independent MAC-VRF.
EVPN Startup Process
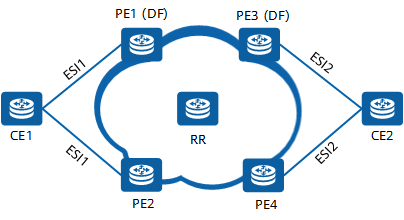
EVPN network topology
As shown in the preceding figure, the EVPN startup process consists of the following steps:
1. Create an EVI.
Create an EVI for each PE and configure the RD and RT attributes of each EVI.
2. Configure BGP peers and enable EVPN.
Each PE sends a Type 3 route to its peers. A Type 3 route contains the RD and label (allocated by MPLS) information.
When a peer receives the packet, it adds the route information to its local BUM traffic forwarding table to guide BUM packet forwarding.
3. Bind the ESI to the EVI.
Bind the generated ESI to the EVI.
Then, each PE starts to send a Type 4 route to its peers. A Type 4 route carries the RD, ESI, and PE source address information.
Peers save received ESI information in the ESI member information table.
4. PEs exchange Type 1 routes to update ESI labels.
After DF election is complete, PEs advertise Type 1 routes to each other. These routes carry ESIs and labels assigned for the corresponding ESIs.
After receiving a Type 1 route from a peer, a PE checks whether the ESI carried in the route is the same as the local ESI. If the ESIs are the same, the PE adds the ESI to its local ES member list.
MAC Address Learning
Assume that CE1 sends an ARP request to PE1.
PE1 learns the MAC address mac1 of CE1 through the forwarding plane and saves the MAC address to its local MAC-VRF.
Then, PE1 generates a Type 2 route to advertise mac1 to other PEs. The Type 2 route carries the RD of the EVI, ESI, mac1, and MPLS label allocated to mac1.
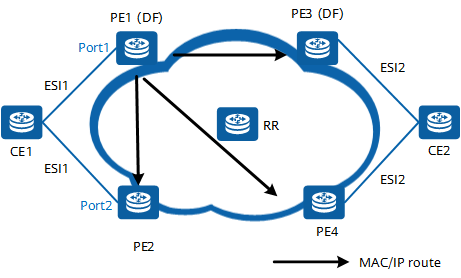
Type 2 route advertisement
On the network shown in the preceding figure, after receiving a Type 2 route from PE1, PE3 and PE4 update their local MAC-VRFs. In this way, PE3 and PE4 learn the MAC address of CE1 through the control plane. PE2, after receiving the route, finds that it carries the same ESI as the local ESI. Therefore, PE2 preferentially selects the route with the local next hop being Port2.
Similarly, PE2 generates a Type 2 route advertising mac1 based on the local MAC address and advertises the route to its peers.
The preceding process enables all PEs to learn the MAC address of CE1.
Traffic Forwarding
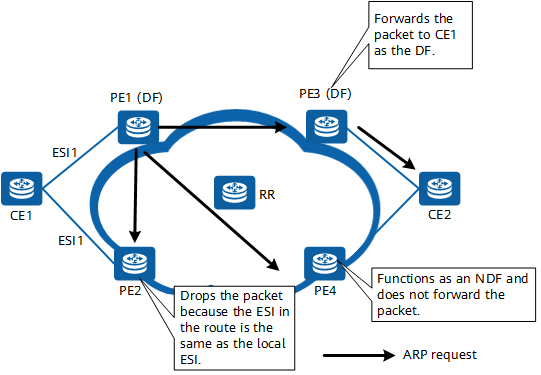
Traffic forwarding
The preceding figure shows how an ARP request sent by CE1 is forwarded to CE2.
After receiving the ARP request, PE1 forwards the packet to all its peers based on the local BUM traffic forwarding table.
After receiving the packet, PE3 removes the tunnel header and determines that the DF is itself. PE3 then forwards the packet to CE2. PE4, which is not a DF, does not forward the packet to CE2.
Upon sending the packet to PE2, PE1 adds PE2's ESI label to the packet because the two PEs have the same ESI. PE2, after receiving the packet, removes the tunnel header and finds that the ESI label in the packet is the same as its own one. PE2 then determines that the packet is sent from the local ES and discards the packet.
Unicast Traffic Forwarding
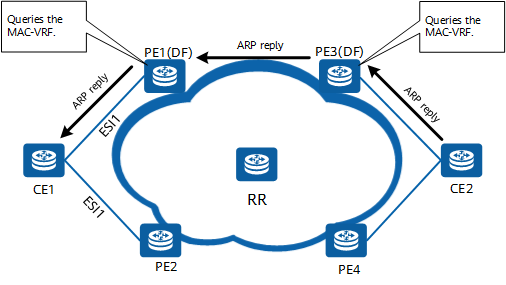
Unicast traffic forwarding
On the network shown in the preceding figure, after receiving an ARP request from CE1, CE2 unicasts an ARP reply to PE3.
After receiving the ARP reply, PE3 learns CE2's MAC address and sends the address to PE1 and PE2 through a Type 2 route. PE1 and PE2 both store the MAC address in the corresponding MAC-VRF.
After receiving the ARP reply, PE3 searches the local MAC-VRF based on the destination MAC address mac1 and finds that the next hops are PE1 and PE2. PE3 then uses the load balancing algorithm to select a path (for example, the path with PE1 being the next hop). After receiving the packet, PE1 removes the tunnel header and searches the local MAC-VRF based on the destination MAC address. After finding that the next hop is Port1, PE1 forwards the packet to CE1 through Port1.
The preceding process covers how CE1 sends an ARP request, CE2 sends an ARP reply, and CE1 receives an ARP reply.
What Are the Typical Applications of EVPN?
PBB
PBB-EVPN is a next-generation L2VPN technology based on MPLS and Ethernet technologies. PBB-EVPN uses BGP to exchange MAC address information between PEs on the control plane and controls the exchange of data packets among different sites across the MPLS network.
A PBB-EVPN service consists of two parts: I-EVPN and B-EVPN. The interface connected to a CE is bound to the I-EVPN instance to provide service access, and the B-EVPN instance connects to the backbone network to manage EVPN routes sent from other PEs.
EVPN VPWS
Similar to traditional virtual private wire service (VPWS), EVPN VPWS provides point-to-point (P2P) services. This solution leverages a simplified version of the original EVPN technology and uses MPLS tunneling to traverse the backbone network without the need for MAC address learning.
On the network shown in the following figure, a VPWS connection is established using attachment circuit (AC) IDs. The local ACID on a PE must be the same as the remote one on the peer PE. Similarly, the remote ACID on the local PE must be the same as the local one on the peer PE.
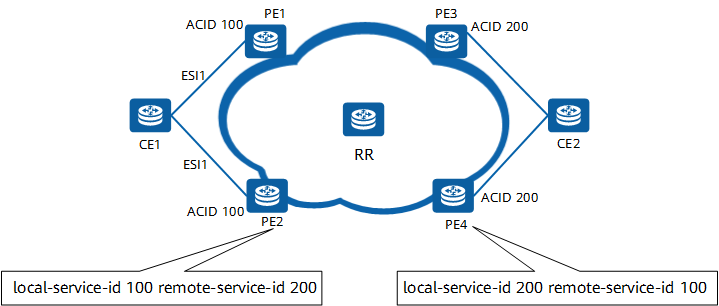
EVPN VPWS networking
EVPN E-Tree
EVPN E-Tree enables you to isolate interfaces that do not need to communicate with each other in the same broadcast domain. As the name suggests, E-Tree is similar to a tree and consists of two roles: root and leaf. The root node can communicate with any leaf node, but leaf nodes cannot communicate with each other. There are three E-Tree service models:
1. Per leaf/root node per PE (also called the instance mode)
As shown in the following figure, a PE can function as only an EVI root or leaf node.
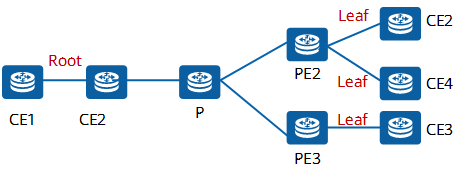
Per leaf/root node per PE
2. Per leaf/root node per AC
As shown in the following figure:
An AC interface can function as only a root or leaf node.
A PE may have both root and leaf AC interfaces.
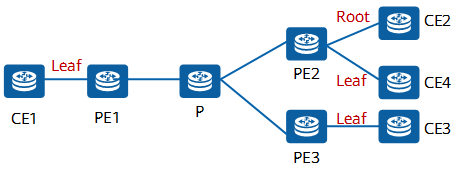
Per leaf/root node per AC
3. Per leaf/root node per MAC
As shown in the following figure:
An AC interface can perform both the root and leaf roles, and the two roles are distinguished by MAC address.
Only unicast traffic, not BUM traffic, is supported.
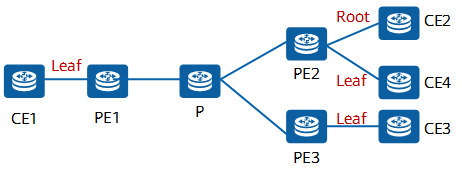
Per leaf/root node per MAC
EVPN L3VPN
At present, the IP bearer network uses complex L2VPN and L3VPN (HVPN) to carry Layer 2 and Layer 3 services, respectively. EVPN, in contrast, can carry both Layer 2 and Layer 3 services. To simplify service bearer protocols, many IP bearer networks will evolve to EVPN. Among them, L3VPN HVPN that carries Layer 3 services needs to evolve to EVPN L3VPN HVPN. EVPN L3VPN has the following advantages:
1. Control plane: Traditional L3VPN uses VPNv4 routes to transmit route information, whereas EVPN L3VPN uses Type 5 routes extended by MP-BGP. EVPN L3VPN unifies the Layer 2 and Layer 3 control planes, simplifying deployment and maintenance.
2. Data plane: Traditional L3VPN and EVPN L3VPN are consistent in implementation.
What is EVPN on Huawei NE40E?
Huawei NE40E Ethernet virtual private network (EVPN) video helps you better understand the background, principles, advantages and applications of the Ethernet VPN (EVPN).
For Product List and Quote: Huawei NE40E Series Routers
 Tags chauds:
réseau
HUAWEI HUAWEI
Routeurs Huawei
EVPN
Tags chauds:
réseau
HUAWEI HUAWEI
Routeurs Huawei
EVPN