































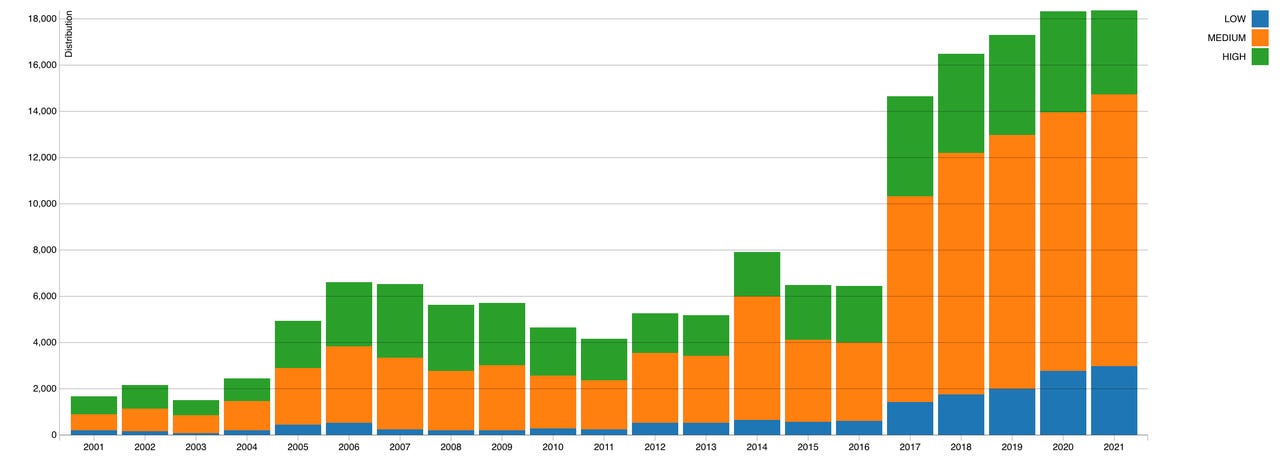
The National Institute of Standards and Technology (NIST) released a graph showing the number of vulnerabilities reported in 2021, finding 18,378 this year.
The figure set a record for the fifth straight year in a row, but 2021 was different in some ways. The number of high severity vulnerabilities fell slightly compared to 2020, with 3,646 high-risk vulnerabilities this year compared to last year's 4,381.
For 2021, the number of medium and low-risk vulnerabilities reported -- 11,767 and 2,965 respectively -- exceeded those seen in 2020.
 NIST
NIST Opinions on the graph were mixed, with some confusion about why fewer high-severity vulnerabilities and others said the report jived with what they saw throughout the year.
A roundup of the best software and apps for Windows and Mac computers, as well as iOS and Android devices, to keep yourself safe from malware and viruses.
Read nowBugcrowd CTO Casey Ellis said that technology itself is accelerating at the most basic level, and vulnerabilities are inherent to software development. The more software that is produced, the more vulnerabilities will exist, Ellis explained.
When it comes to the breakdown of high, medium and low-severity vulnerabilities, Ellis said lower impact issues are easier to find and are generally reported more often, with the opposite being true of high impact issues.
"High impact issues tend to be more complicated, remediated more quickly once found, and -- in the case of systemic high-impact vulnerability classes -- are often prioritized for root-cause analysis and anti-pattern avoidance in the future, and thus can often be fewer in number" Ellis said.
Pravin Madhani, CEO of K2 Cyber Security, said the lower numbers of high severity vulnerabilities may be due to better coding practices by developers, explaining that many organizations have adopted a "shift left" in recent years and seek to put more of an emphasis on ensuring security is a higher priority earlier on in the development process.
The overall increase in reported vulnerabilities was due in no small part tothe COVID-19 pandemic, which forced almost every organization globally to adopt technology in one way or another, Madhani added.
"The ongoing COVID-19 pandemic has continued to push many organizations to rush getting their applications to production, as part of their digital transformation and cloud journeys, meaning the code may have been through less QA cycles, and there may have been more use of 3rd party, legacy, and open source code, another risk factor for more vulnerabilities," Madhani said. "So while companies may be coding better, they're not testing as much, or as thoroughly, hence more vulnerabilities made it to production."
Other cybersecurity experts like Viakoo CEO Bud Broomhead said the report was alarming because of how many exploitable vulnerabilities remain "in the wild" for threat actors to take advantage of.
The record number of new vulnerabilities, combined with the slow pace of patching and updating devices to remediate vulnerabilities, means that the risk is higher than ever for organizations to be breached, especially through unpatched IoT devices, Broomhead added.
Vulcan Cyber CEO Yaniv Bar-Dayan said that what concerned him most was the mounting pile of security debt that cybersecurity professionals can't seem to get ahead of.
If IT security teams are leaving 2020's vulnerabilities unaddressed, the real 2021 number is cumulative and becoming harder and harder to defend against, Bar-Dayan explained.
"We are seeing more advanced persistent threats like the SolarWinds hack that daisy chain vulnerabilities and exploits to inflict maximum damage to digital organizations. As an industry, we are still learning from and cleaning up after that one. And it is unfair to put all the blame on SolarWinds considering how the bad actors used known, old, unaddressed vulnerabilities that should have been mitigated by IT security teams well before the SolarWinds software supply chain hack was ever hatched," Bar-Dayan said.
"Cybersecurity teams need to do more than just scan for vulnerabilities. We need to work together as an industry to better measure, manage and mitigate cyber risk, or we will be crushed by this growing mountain of vulnerability debt."
 Tags chauds:
technologie
La sécurité
Tags chauds:
technologie
La sécurité