































What a time to be alive! Hot on the heels of Forrester's release of our definition of modern Zero Trust (ZT), the US Office of Management and Budget (OMB) released a memo entitled Moving the US Government Toward Zero Trust Cybersecurity Principles.
Coincidence? Yes. A big deal? Also, yes.
If executed as mandated, not only will government agencies meet the security maturity levels of large organizations in the private sector (they did just start hiring at that level, remember), they'll also surpass them. This major transformative effort sets a new bar for all sectors and is a cause for celebration. It also breaks down barriers to Zero Trust adoption by providing security leaders across industries a set of priorities in line with each of the five Zero Trust pillars, which they can seek executive buy-in -- made all the easier by a high-profile government mandate -- and build into their budgets and timelines.
Zero Trust advocates should be jumping for joy over the federal government's understanding of modern Zero Trust and how it is operationalized. Forrester designated seven operational domains of Zero Trust: five for security controls and two for interaction across the domains when we created Zero Trust eXtended (ZTX). The Cybersecurity and Infrastructure Security Agency (CISA) and the OMB recognize these seven and add one more: governance.
So, for the past decade, where there was previously much confusion around how to define or operationalize Zero Trust, today there is an outpouring of aligned definitions, thanks to the White House Executive Order released in early 2021. Importantly, CISA's view takes cues from Forrester's original shaping of Zero Trust when we first defined it over 12 years ago. Our guns are pointing in the same direction.
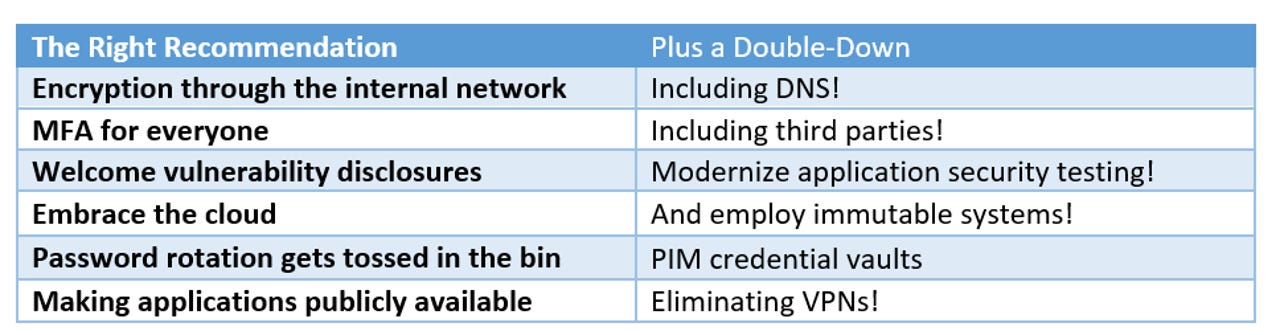
Second, the OMB strategy document has depth and breadth. In all these domains, OMB doesn't just make the right call, it makes the bold call and doubles down on Zero Trust. Examples abound!
 Forrester
Forrester There are a handful of half measures, which is fewer than we were expecting for government IT composed largely of islands of varying technological maturity. This includes encrypted email and some leeway on how people do ZT in the network (which is understandable, because the network is still the hardest part).
Many organizations lack a cogent cybersecurity strategy; at least now US federal agencies aren't among them. And while better cybersecurity is a worthy goal, don't forget that sabers rattle in both a middle kingdom and the remains of a superpower, neither of which have qualms about cyber warfare.
For many initiatives, the devil is in the details. That's not true for the OMB Zero Trust strategy; as we mentioned above, it'sreally good. Here, the devil will be in the execution. To what extent will every agency, contractors, and all their subcontractors operationalize Zero Trust?
Among the timelines included in the OMB strategy are several short-term tasks, such as providing CISA and the General Services Administration any non-.gov hostnames (a mere 60 days) and the welcoming of external vulnerability reports for internet-accessible systems. Within one year, enforced password rotation should be kicked into the gutter, where it belongs.
Crucially, within 60 days, agencies must submit to OMB and CISA an implementation plan for FY22
 Tags chauds:
technologie
La sécurité
Tags chauds:
technologie
La sécurité