


















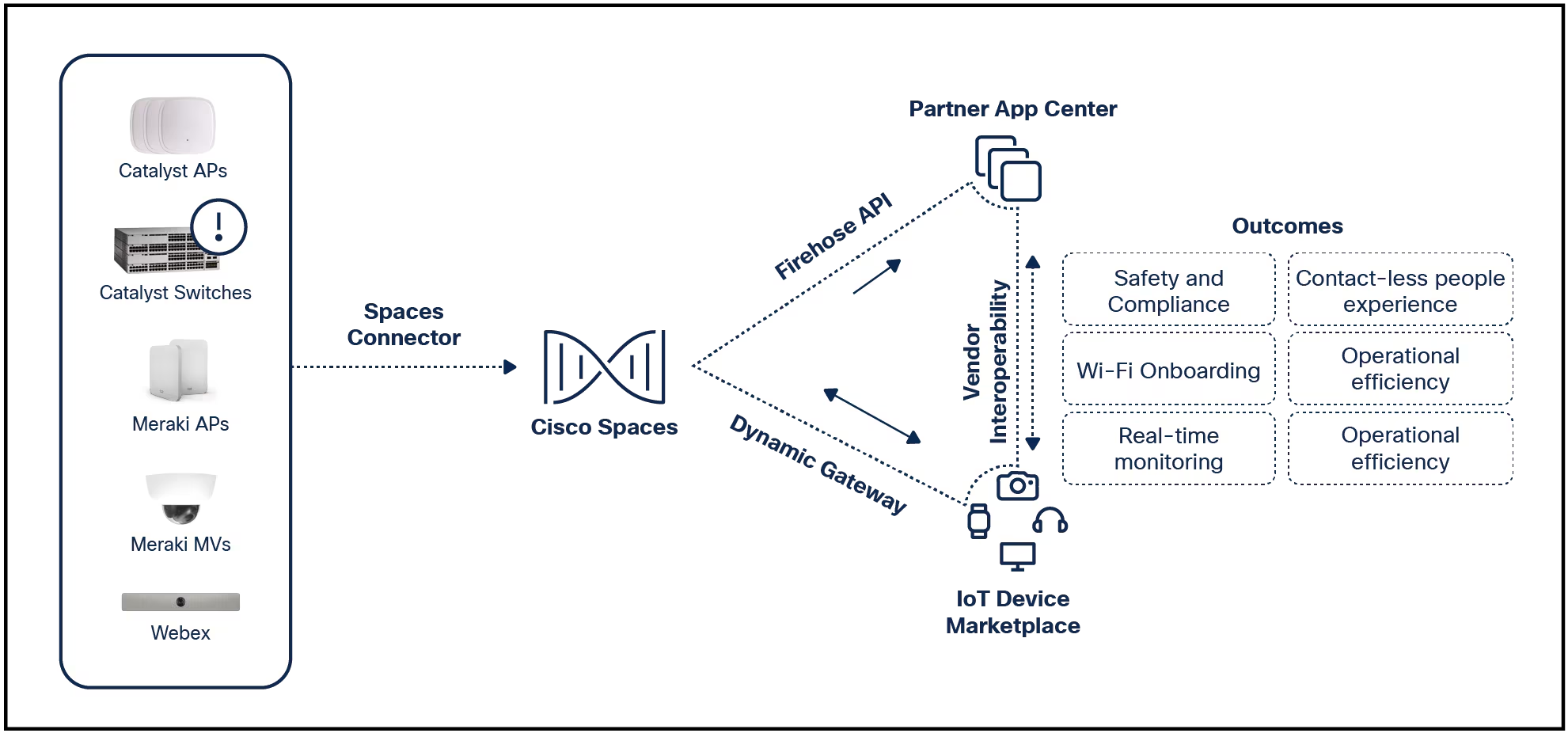

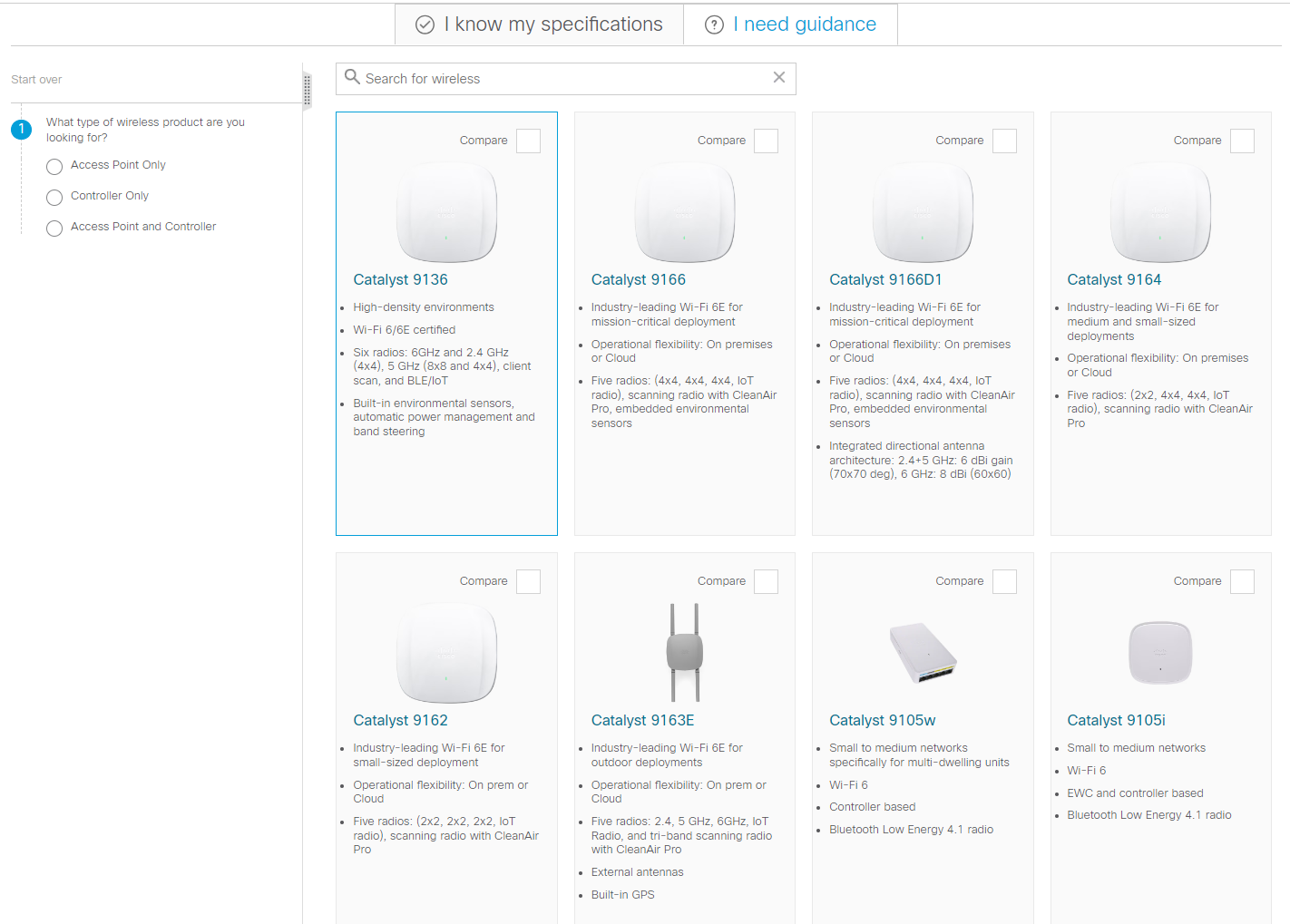
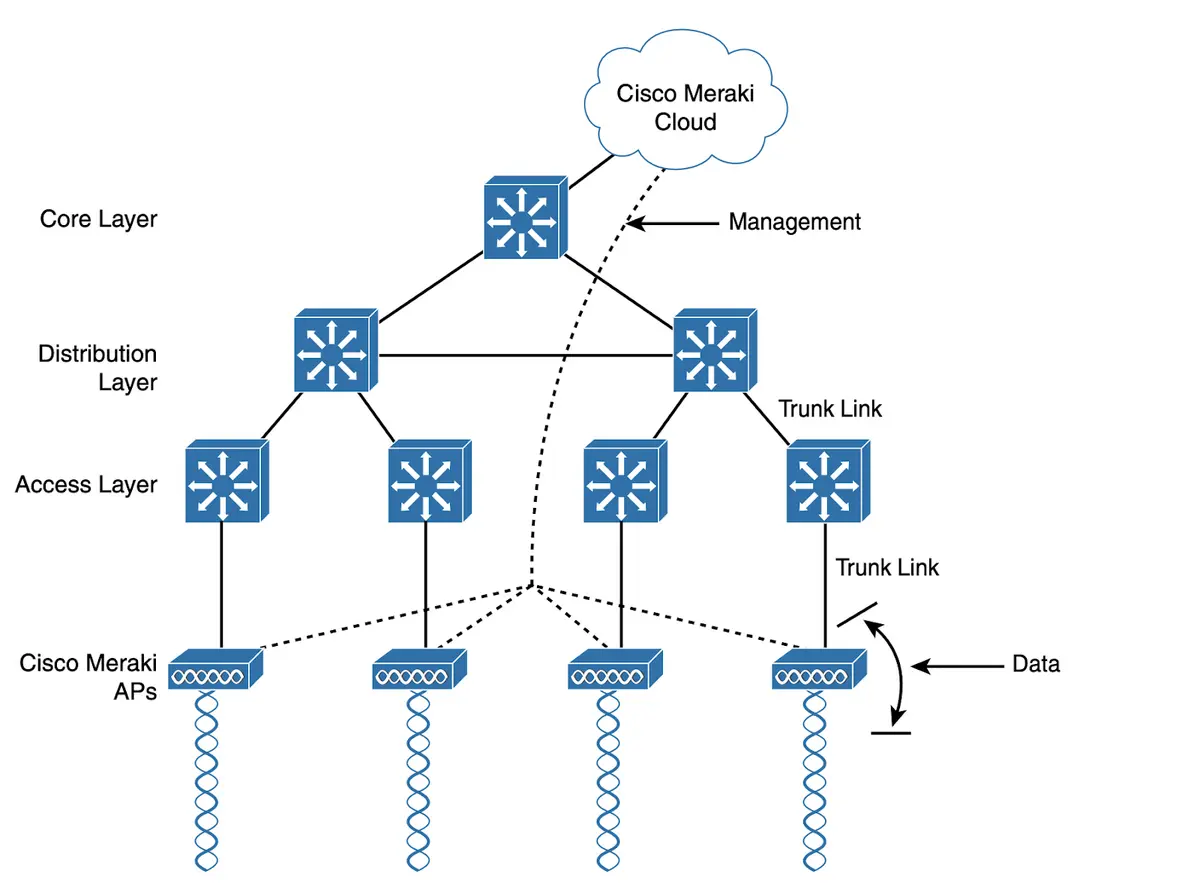






Intel estimates1that one-third of the servers in production are more than four years old. At first, one might think that it is great to get this much service out of a capital investment, but the operational costs to run these outd...

Cryptography is critical to secure, trustworthy communications. Recent questions within the tech industry have created entirely new discussions about the cryptography underpinning our communications infrastructure. While some in t...

Now when I'm talking about safekeeping a mobile device, I'm not saying don't use your Kindle by the pool or let your toddler play on the iPad while eating ice cream. These are dangerous things to be doing with a gadget, but today ...

This is the latest in a series of posts featuring partner success stories where partners share how they're helping customers achieve their goals by using Cisco technology. This week we're pleased to feature Scott Alexander, Presid...

Recently, I was chatting with Hugo Vliegen, Director of Technical marketing, Enterprise Networks, and he was telling me all of the questions he had been getting from customers about the Cisco UCS E-Series. Questions such as:...

One of the basic tenants of enterprise mobility is its direct influence on "now". When organizations implement mobile policies like BYOD and virtualized desktops, day-to-day operations can immediately improve. In most cases, the r...

Guest post by Txomin Barturen, Senior Consultant -CTO Office, EMC Corporation SQL Server provides customers with a vast array of technology options to address a diverse range of data and reporting requirements including extremely ...

The We're Listening blog series has tracked some of the new programs and capabilities Cisco is introducing to make it easier to do business with us. The corporate Ease of Doing Business (EoDB) Program drives many of these improvem...

Science fiction writers have often mused about the merger of humans and machines. But while RoboCops and bionic superheroes aren't likelytofight evil anytime soon, some excitingwearablesmart technologies are already here. They may...

At the GSMA Connected Women Event on October 10-11, I had the thrill of combining two of my favorite things -being in New York and speaking about women in technology. Both ignite a passion in me. As a little girl, when hearing the...

Many Cisco customers with an interest in product security are aware of our security advisories and other publications issued by our Product Security Incident Response Team (PSIRT). That awareness is probably more acute than usual ...

I recently had the honor to speak at the Small Cells Forum in Dubai. One thing is certain:Wi-Fi and small cells are certainly important throughout the Middle East and Northern Africa. Operators from throughout the region cam...