






























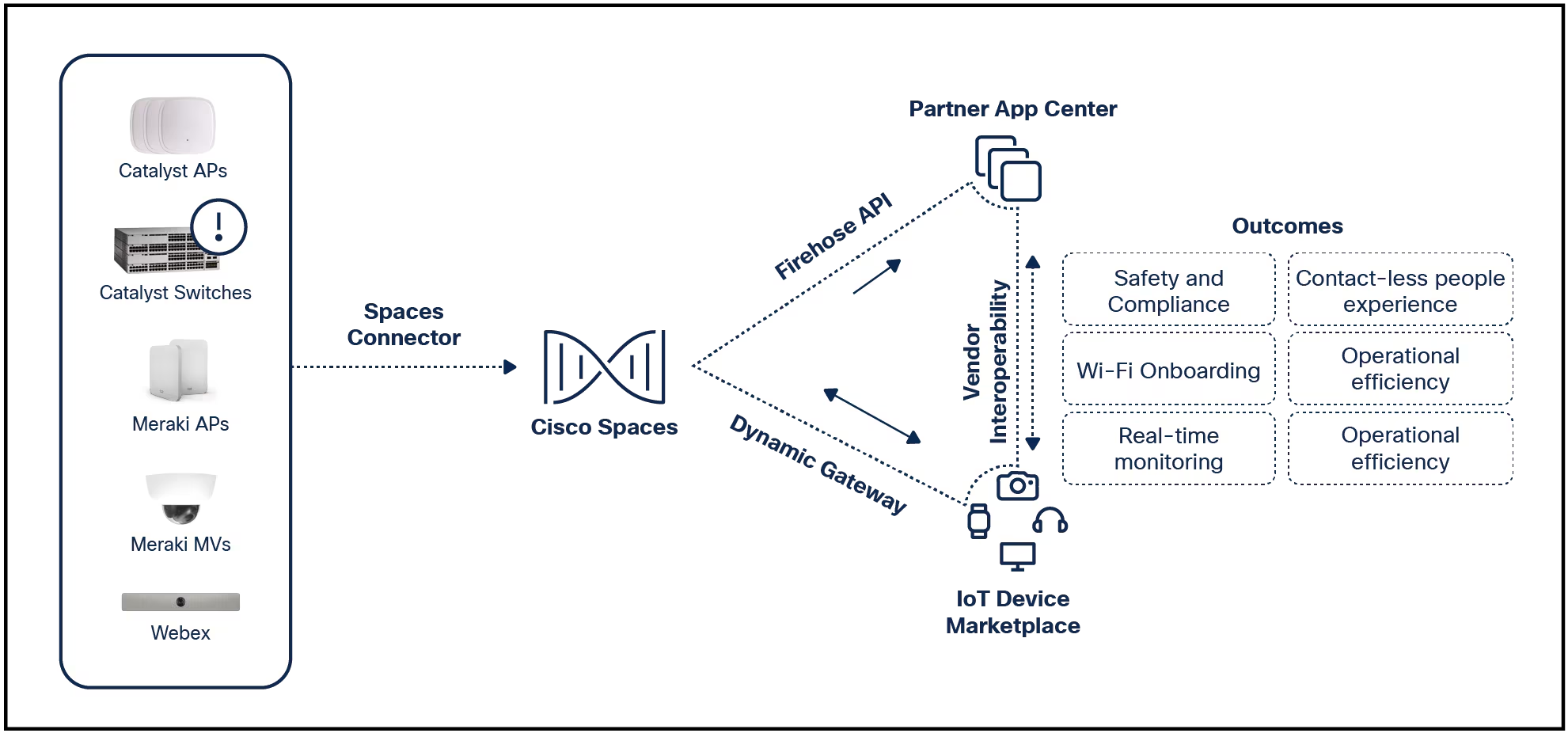

The next step in intent-based networking is putting it in more places. We launched our intent-based networking portfolio a year ago with the introduction of the Catalyst 9000 line of switches and Cisco DNA Center. These products s...

In my last blog, I told you we would have lots of exciting announcements at Connections 2018. Well, I'm happy to share some of the highlights of today's exciting news with you. Strong execution The past year has been very strong....

They say there's strength in numbers. How's this one for you? Cisco's collaboration portfolio serves over 300 million people worldwide -and counting. Our technology solutions are changing lives, setting the standard for how people...

I love the line for 1-800 Contacts,Delivering contact lenses to people who woke up and realized, "[CURSE WORDS], I'm down to my last pair!" since 1995. It demonstrates their customers' urgency, with humor, for immediate help from ...

A little over a year ago, I went to a Cisco board meeting. I was presenting a proposal to acquire BroadSoft for a sum of approximately USD$1.9B. In the meeting, Cisco board members combed through the detail of my presentation. As ...

History|of|WAN circuits I still remember the mid to late 1990s and my first interactions with the Internet. At that time I had my Pentium personal computer for around a year and Windows 95 was all the rage. And while Solitaire and...

We have the emergence of a new urban services industry that is enabled by 20B+ real-time sensors and mobile data sources providing contextual data and creating$3T of value for Cities through improved citizen services, reduction in...

The Golden Gate Bridge was built to connect San Francisco and Marin County using a suspension bridge over a mile long. It was built during the Great Depression and took over 4 years to construct with over 1.2 million rivets....

The pace of change is accelerating, with multiple trends converging to stress service providers' network and IT infrastructure as we move towards 2019. The average service provider infrastructure must carry a heavier workload in t...

How to protect your endpoints from "creepy crypto miners" Here's what's creepy about cryptocurrency mining threats. It can lead to the slow death of your computers -capable of literally melting smartphones in some cases -by overwo...

As any security consultant will know, the more fun you have on an engagement (see part 1, part 2 and part 3 for the back story), the longer the report will be afterwards and the more important the executive and technical summaries...

Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Nov. 02 and Nov. 09. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the th...