































Packet capture has long been used by network operators, but a variety of challenges have limited its effectiveness in security and threat detection. In large networks, packet capture can collect terabytes of packet data, and sifti...

Contributions to this post are also made by Jon-Paul Pritchard, Head of Executive Staffing in the Asia Pacific Japan and China (APJC) region. This week, I and my Cisco colleague Jon-Paul Pritchard will be driving a TUK TUK -which ...

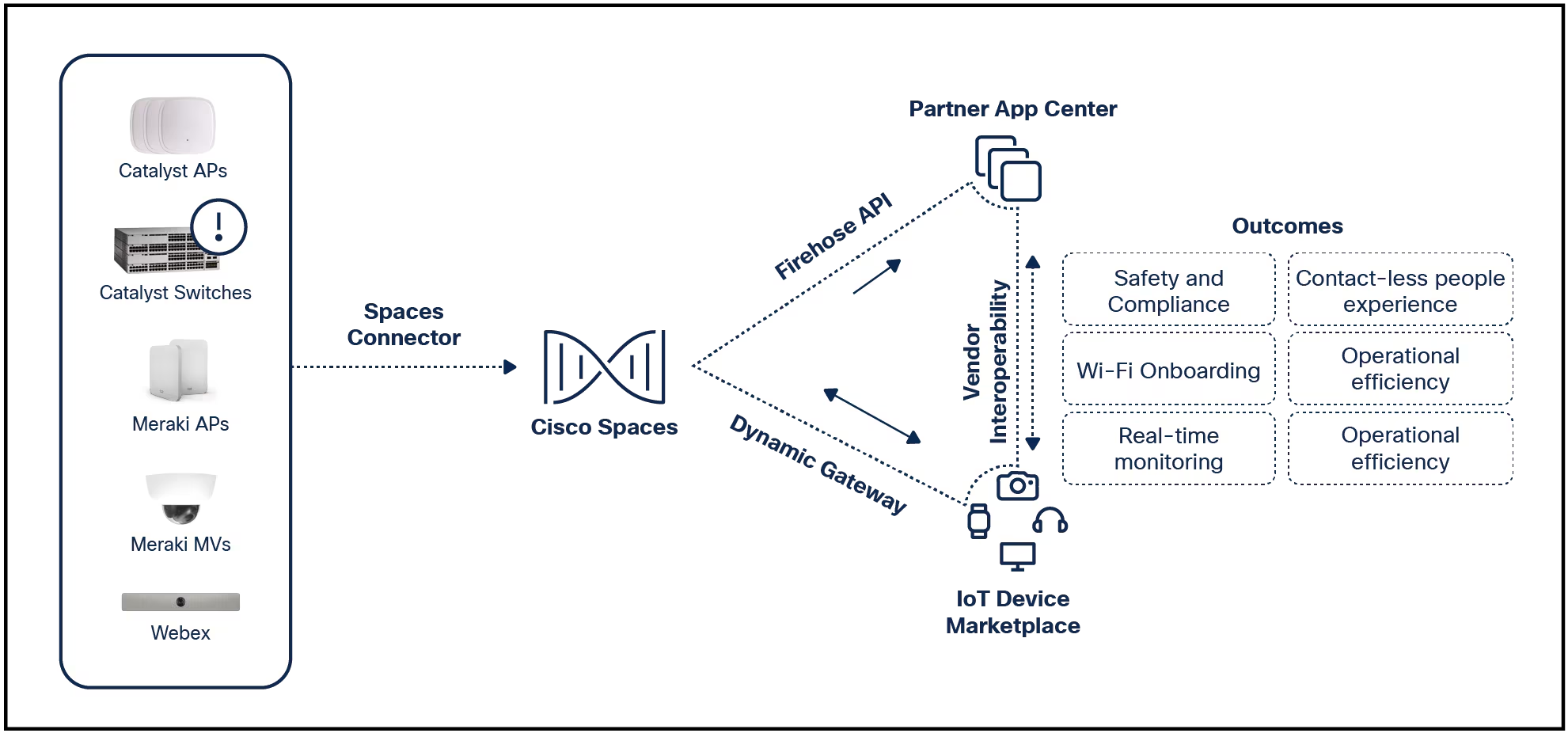
"We adore chaos because we love to produce order." -M.C. Escher "Alexa, turn on Apple TV" "Alexa, turn on dining room lights" "Alexa, play classical playlist from Spotify" "Alexa, set the living room to 70 degrees" Our household i...

Today, Talos is publishing a glimpse into the most prevalent threats we've observed between March 24 and March 31. As with previous round-ups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the...

The Olympic Games represent the pinnacle of athleticism and excellence on the world stage like no other event. The scale of the preparation and production that goes into them is absolutely massive. That's why providing connectivit...

This post authored by Nick Biasini with contributions from Edmund Brumaghin and Alex Chiu The last time Talos discussed Sundown it was an exploit kit in transition. Several of the large exploit kits had left the landscape and a co...

'...It takes abigvillage...' so to speak when it comes to bringing enterprise-class big data & analytics solutions to the market. It is for this reason that our Cisco UCS team partners with several key ISVs in the big data se...

You can draw right on Cisco Spark Board. And on the wall...Things were a bit quieter at Enterprise Connect today as the event came to a close with a few morning sessions and the final summary panel concluding at noon. Panels Bots,...

On March 29, Cisco became aware of several customer outages involving different releases and models of Cisco ASA and Cisco Firepower Threat Defense (FTD) appliances. Cisco has published a Field Notice urging Cisco customers w...

A year ago, I introduced our Enterprise NFV solution. This year at CiscoLive Berlin (#CLEUR), we announced solutions that extend virtualization beyond the branch, across the entire enterprise network and to the cloud. Every d...

Our market economy, which produces goods and services and jobs for billions around the world, is built on the foundation of a strong commercial law system -a foundation that promises "a deal is a deal", that rights and obligations...

In addition to having the coolest name for a generation in decades, millennials are a huge target market for our partners and their customers. Our ISV partners like Turnstyle are helping customer tap into that market by building W...