






























This post walks through the models for building resilient applications on OpenStack infrastructure with Cisco Metacloud, OpenStack Orchestration, and configuration management tools like Ansible. Agile Infrastructure, Some Backgrou...

When people think about the impact of technology on education, they tend to focus on how the Internet has changed the classroom experience. Blended learning is now a common delivery model in universities and vocational education, ...

Fun fact: as many of you know, I am an avid triathlete. Not only do I constantly strive to achieve my personal best but I also like to encourage others to achieve their goals! About five years ago, I started a running group in Tam...

Patch Tuesday has once again arrived! Microsoft's monthly release of security bulletins to address vulnerabilities provides fixes for 37 newly disclosed security flaws. Today's release sees a total of 10 bulletins with five of the...

Guest post by Matt Melton, BlueLine Grid The International Association of Chiefs of Police (IACP) annual convention will kick off during the third week of October 2016 in San Diego. Planning is in full gear, and Cisco is highlight...

#CiscoChampion Radio is a podcast series by Cisco Champions as technologists. Today we're discussing VCS Expressway. Get the Podcast Listen to this episode Download this episode (right-click on the episode's download butto...

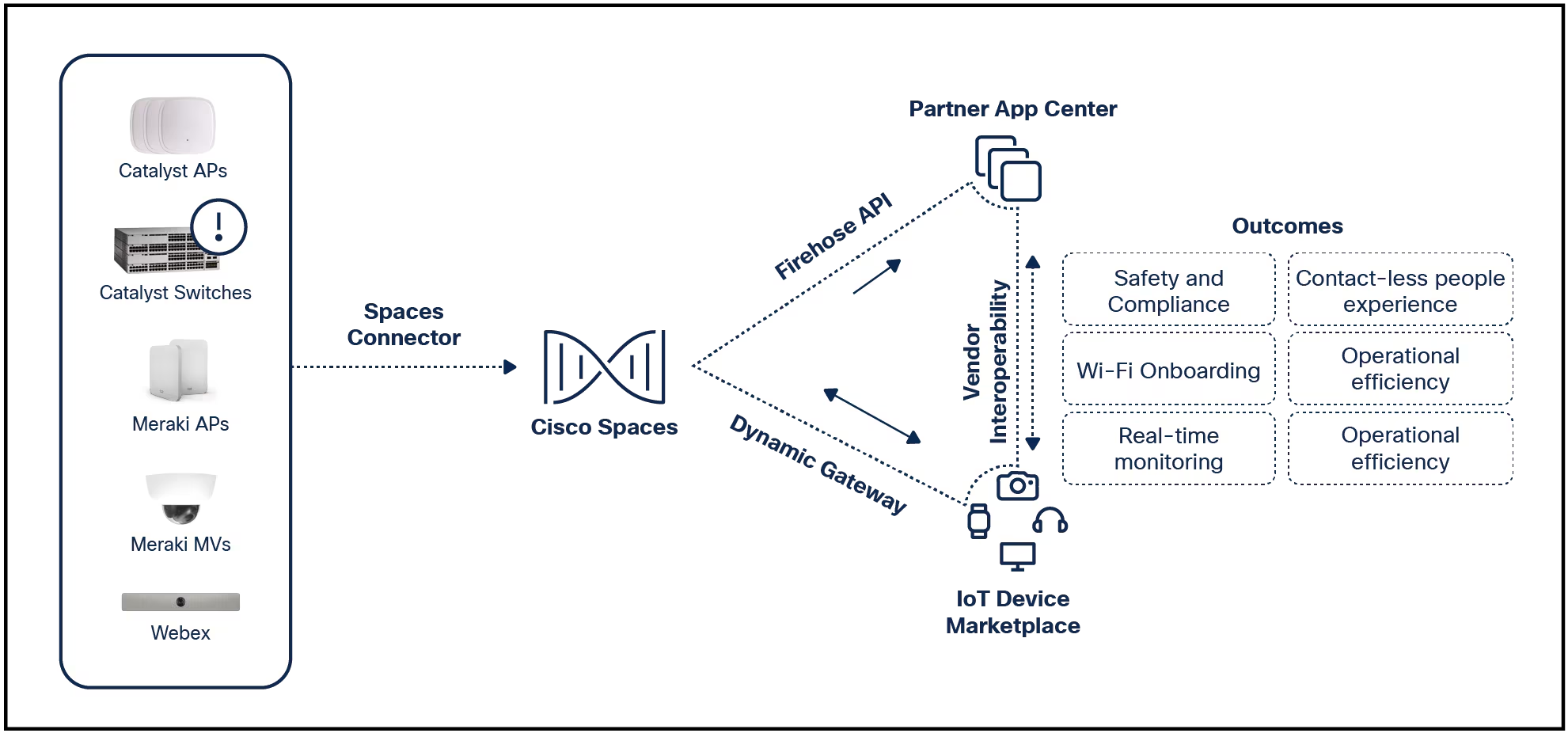
Six months ago, Cisco announced the Digital Network Architecture (DNA), providing companies with infrastructure capabilities necessary to digitize their businesses. At the core of DNA are four guiding principles: Virtualizenetwo...

We've all heard it by now: Digital disruptors will replace 4 in 10 incumbent companies over the next five years. That's a statistic certain to make even the Fortune 50 feel squeamish. Companies are rushing to keep pace and transfo...

Our lives demand digital engagement. In a world where almost any experience can be delivered in an instant, real-time information and access is now an expectation, especially in the healthcare industry. I've been studying the chal...

Cisco Intern David Black shared this post with us before he returned back to school. We wish all of our interns a very successful year ahead of them! *** No, my name isn't Waldo. But when I started my internship at Cisco, I felt ...

Since I started this blog series about corporate innovation and intrapreneurship, readers often ask which of my nine building blocks is most essential to mobilize an innovation disruption across an entire company. Which is the cor...

For every young woman who wants to pursue a career in science, math, engineering, or technology (STEM), look no further than Ada Lovelace. Born in 1815 at the heart of the Industrial Revolution, she gravitated toward the fascinati...