



























It sounds a bit of an oxymoron -Securing and Explosive. Indeed, security is what enables growth, actually, explosive growth in video delivered to multiscreen devices. Video viewing will make up 80% of global IP traffic by 2019, ac...

Interest in Software Defined Networking (SDN) continues to grow through the ability to make networks more programmable, flexible and agile. This is accomplished by accelerating application deployment and management, simplifyi...

The rise of malware created specifically for endpoints like mobile devices is forcing IT Security teams to focus increasingly on endpoint security solutions. According to a survey by the Ponemon Institute[1] published in January, ...

Today was another busy day in a city by a bay. With the Cisco Live gears fully engaged, there were more sessions, more classes,andmore of everything going on. Our product teams did presentations and trainings throughout the day. A...

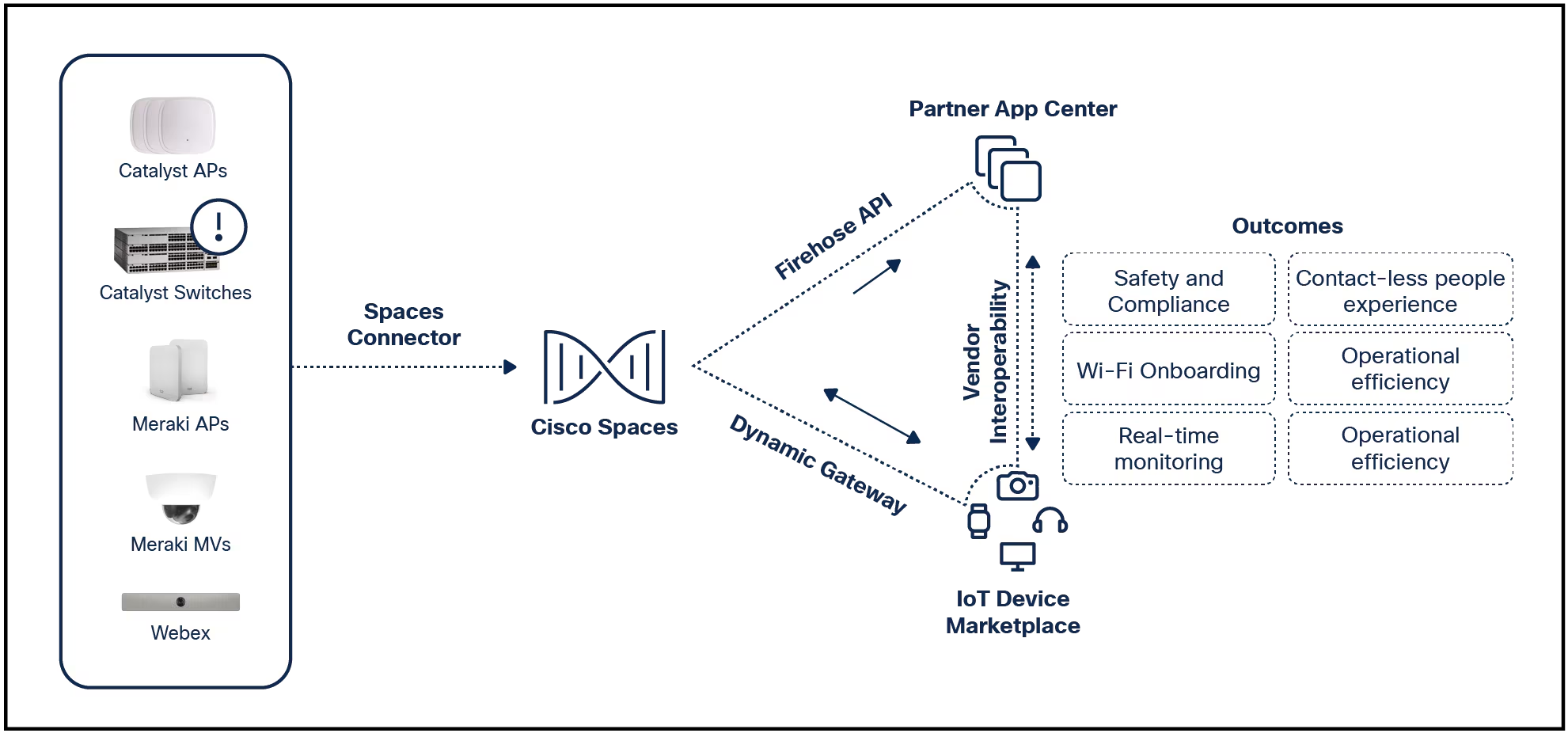
Blog written by Stefan Vallin, Principal Engineer, Cisco Systems Consider the three key steps related to provisioning and maintaining a customer network service. First, configuration of network devices according to the service int...

On behalf of the development team. I'm pleased to announce the 0.3.0 release of Microservices Infrastructure. In the weeks since 0.2, we've added a number of features and improvements. The software can be downloaded at: https://g...

#CiscoChampion Radio is a podcast series by Cisco Champions as technologists. Today we're at Cisco Live San Diego (#CLUS) talking about highlights and take-aways from the event so far. Listen to the Podcast. Learn about the Cisco...

As IT organizations look to the cloud to become more efficient and achieve the agility their business demands, one of the biggest security challenges they typically face is right at the heart of any enterprise -the data center. In...

DDoS attacks are no longer just a nuisance and they can cause lasting damage. Organizations that ignore this threat often learn the high costs involved in the damage from these attacks -ranging from mild service degradation and to...

The recent passing of John Forbes Nash made me wonder how his ingenious game theory can be applied to technology innovation. Very simply put, Nash's theory of equilibrium puts forth that outcomes are more attainable for all partie...

Today, Microsoft has released their monthly set of security bulletins designed to address security vulnerabilities within their products. This month's release sees a total of 8 bulletins being released which address 45 CVE. Two of...

Yesterday, over 25,000 Cisco customers, employees, and executives helped kick off Cisco Live US 2015 in San Diego, California, attending everything from John Chambers' final keynote to the World of Solutions in the massive San Die...